Description
In today’s digital landscape, cybersecurity breaches have become a pressing concern for individuals and organizations alike. This document delves into the intricate details of a cybersecurity breach, exploring its stages, common tactics employed by cybercriminals, and the implications for affected entities. By understanding the anatomy of a breach, stakeholders can better prepare and respond to potential threats.
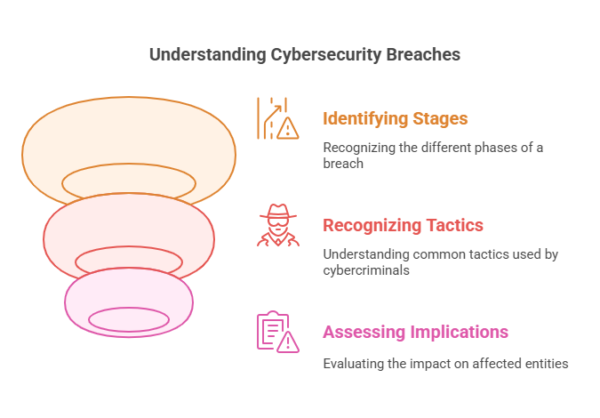
Stages of a Cybersecurity Breach
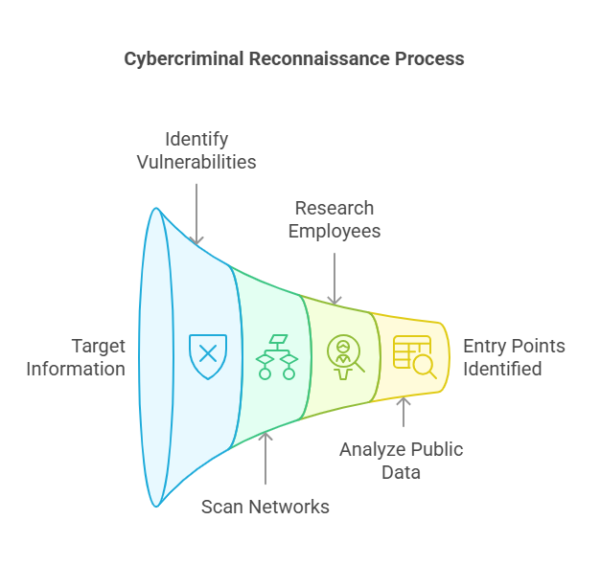
Reconnaissance:
Cybercriminals gather information about their target, identifying vulnerabilities and potential entry points. This may involve scanning networks, researching employees, and analyzing publicly available data.
Initial Compromise:
Attackers exploit identified vulnerabilities to gain unauthorized access. This can occur through various methods, including phishing emails, malware, or exploiting software flaws.
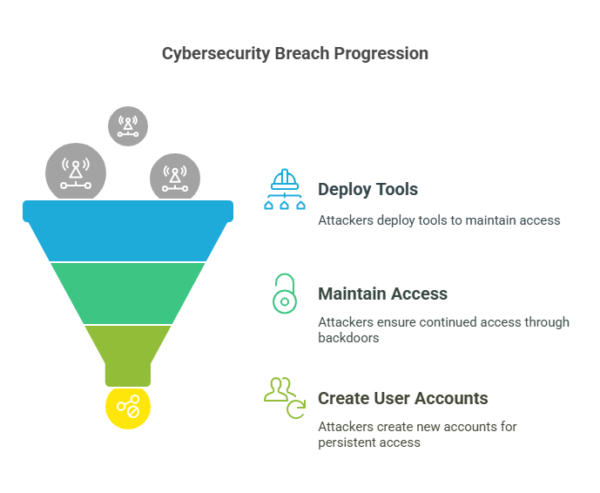
Establishing a Foothold:
Once inside the network, attackers deploy tools to maintain access. This may involve installing backdoors or creating new user accounts to ensure they can return even if the initial vulnerability is patched.
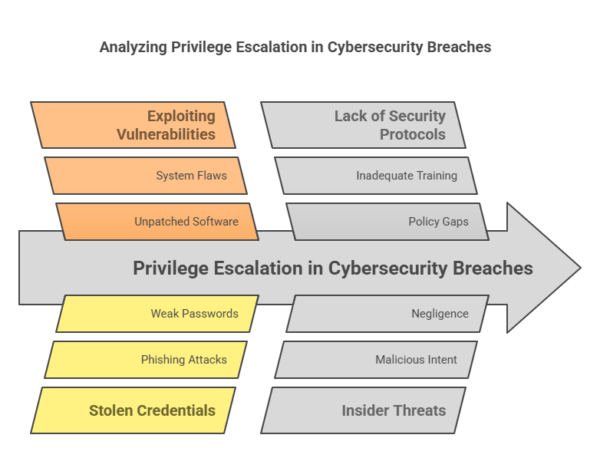
Privilege Escalation:
Cybercriminals seek to gain higher levels of access within the system. This can involve exploiting additional vulnerabilities or leveraging stolen credentials to access sensitive data.
Data Exfiltration:
At this stage, attackers extract valuable information from the compromised system. This could include personal data, financial information, or intellectual property, which can be sold or used for further attacks.
Covering Tracks:
To avoid detection, cybercriminals often take steps to erase their presence. This may involve deleting logs, altering timestamps, or using encryption to obscure their activities.
Post-Breach Activities:
After a breach, attackers may continue to exploit the compromised system or sell access to other criminals. Organizations may face reputational damage, legal consequences, and financial losses as a result of the breach.




Reviews
There are no reviews yet.